When Meta breaks: A Maltese publisher's account vanishes, support collapses, and the fight begins
When the Facebook account of Anthony P. Bernard, Be Communications' managing director and editor, was hacked, he expected a recovery process — not a digital maze. What followed was months of conflicting decisions, vanished business pages, a fictitious Instagram "violation", a fake hacker appeal link, and support loops that led nowhere. He explains how one hack spiralled into a full-blown business risk — and why he's still fighting for accountability.
For twenty years, Facebook was just there in the background of my work. It was never the star of the show, just the stage light that was always on. My company, Be Communications Ltd, runs several magazine brands – Money, Skipper, Techmag, Femme, Foodist – and all of them relied on my personal Facebook profile to exist in Meta's world: one login, one ad account, one quiet bit of infrastructure connecting everything.
On 27 August 2024, that light went out.
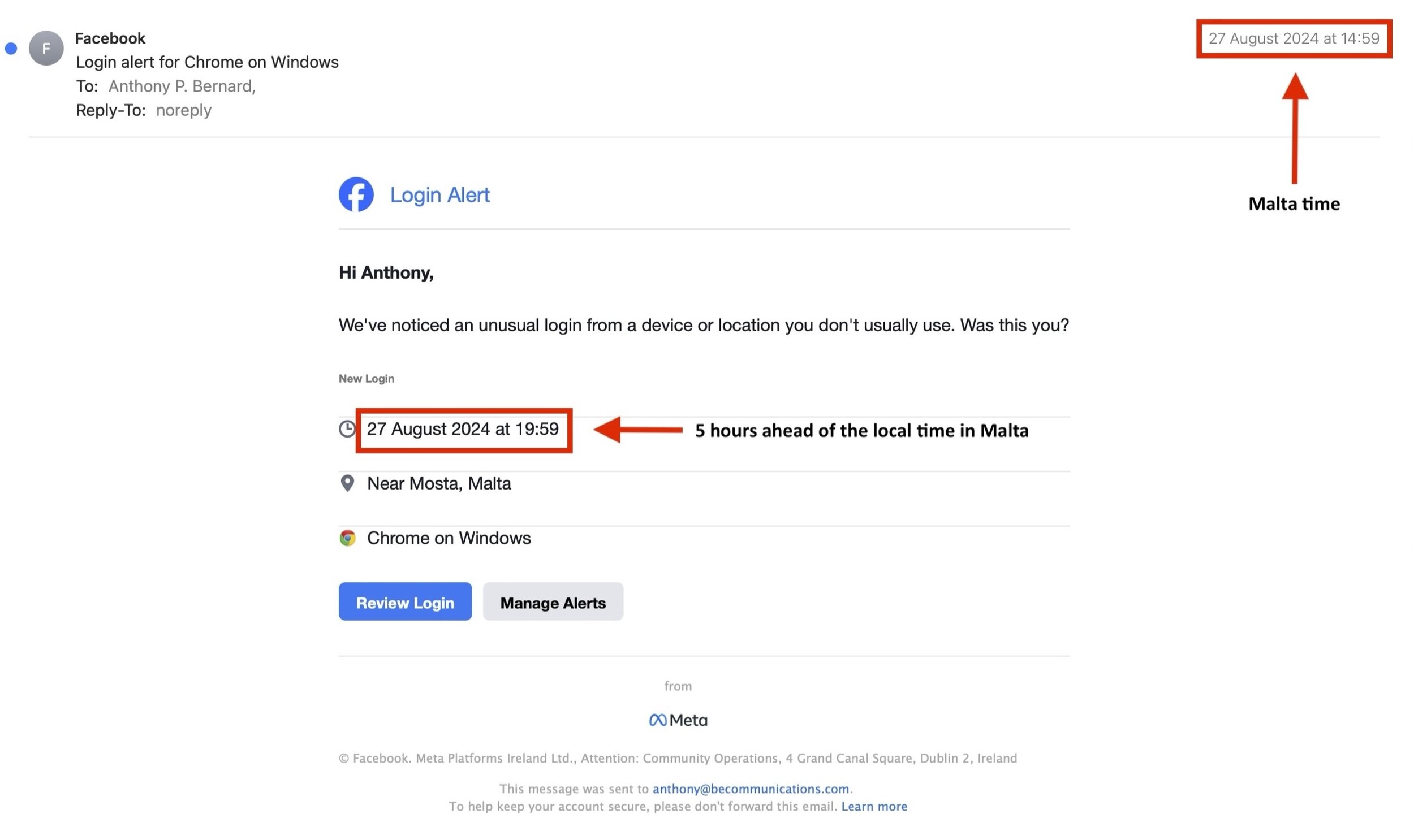
It started with a routine email from Facebook, the kind you almost swipe away without reading: "Someone may have accessed your account." Annoying, but familiar. Nine minutes later, a second email arrived, this time claiming there had been a login from Mosta at 19:59. The email itself was timestamped 14:59. Unless Malta had quietly shifted its timezone by five hours, something was already off.
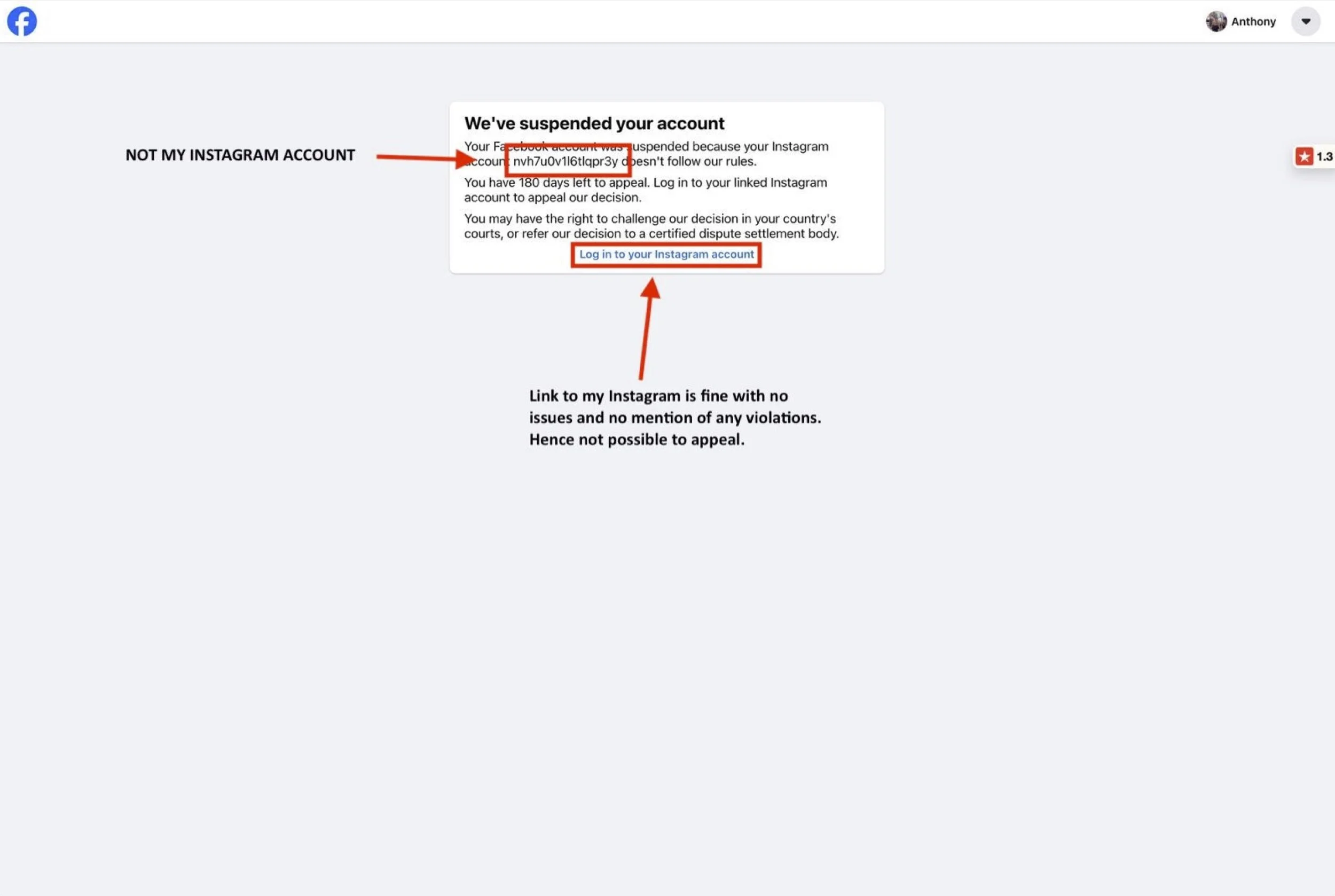
I tried to log in and hit a wall. My account was suddenly suspended. No warning, no countdown, no "are you sure?" Just gone. And the reason was even stranger: according to Facebook, my profile had been linked to an Instagram account with the handle "nvh7u0v16tlqpr3y".
If you're reading that twice, so did I. It doesn't look like a name. It looks like a password generator had a stroke. I had never seen it before. Yet Meta's system insisted that this nonsense handle was now my Instagram account – and that "I" had broken the rules there.
The screen told me I could appeal, but only by logging into that Instagram account. When I clicked the link, expecting to land on some weird profile, it took me instead to my own real Instagram – the one I actually use and still control. There were no warnings, no violations, no appeal forms. Nothing to fix because, on that side of the fence, nothing was broken.
So I was trapped in a loop. Facebook said I was guilty because of an Instagram that wasn't mine. The appeal link pointed me to my real Instagram, which wasn't guilty of anything. And there was no way to tell the system it had simply got the wrong person.
At first, I thought this was some brand-new hack targeting me personally. Then I did what everyone does: went down a late-night Reddit rabbit hole. It didn't take long to realise that this was not new at all. People had been describing the same pattern for years: bogus, machine-generated Instagram handles suddenly attached to their Facebook accounts; appeal links that led nowhere; support loops that went in circles. It's a known exploit, widely discussed, with victims swapping screenshots like war stories – and yet Meta has never publicly admitted it, let alone patched it.
That was unsettling enough. What made it worse was the timing. In the months before the hack, I had been posting quite a bit of pro-Palestine content. Some of the videos had their audio stripped without explanation, the kind of quiet censorship many creators experienced during that period before Meta slightly relaxed its stance. I can't prove that my content and the hack are connected. But it's hard to ignore the coincidence: a known backdoor exploit that's been allowed to linger for years, plus people inside or around Meta offering "paid recovery services", plus accounts that are not exactly towing the line getting suddenly wiped out of the system.
When the suspension hit, it didn't just take my personal account. It took the entire backbone of my digital business. The main ad account went down with it. Access to the Money, Skipper, Foodist, FM, Techmag, Be Communications and Flip Flop Store pages vanished. I couldn't post, couldn't schedule, couldn't boost, couldn't see analytics, couldn't respond to messages. To the outside world, the pages were still there. They may as well have been on another planet.
What followed was less a support experience and more a stress test of how much bureaucracy a human being can take. Case after case was opened with Meta. I lost count of how many times I uploaded my ID. I sent company registration documents, invoices showing the ad account billed to Be Communications, screenshots of the pages, and proof that the domains in the page info pointed to my servers. I even subscribed to Meta Verified on a new profile, hoping it would unlock a more competent level of assistance.
It unlocked more conversations, that much is true. But not solutions.
The conversations blurred into each other: "We're reviewing your case." "Please be patient." "We could not verify." "Please upload your ID again." It felt like trying to explain a complex medical condition to a chatbot that only knows how to prescribe paracetamol.
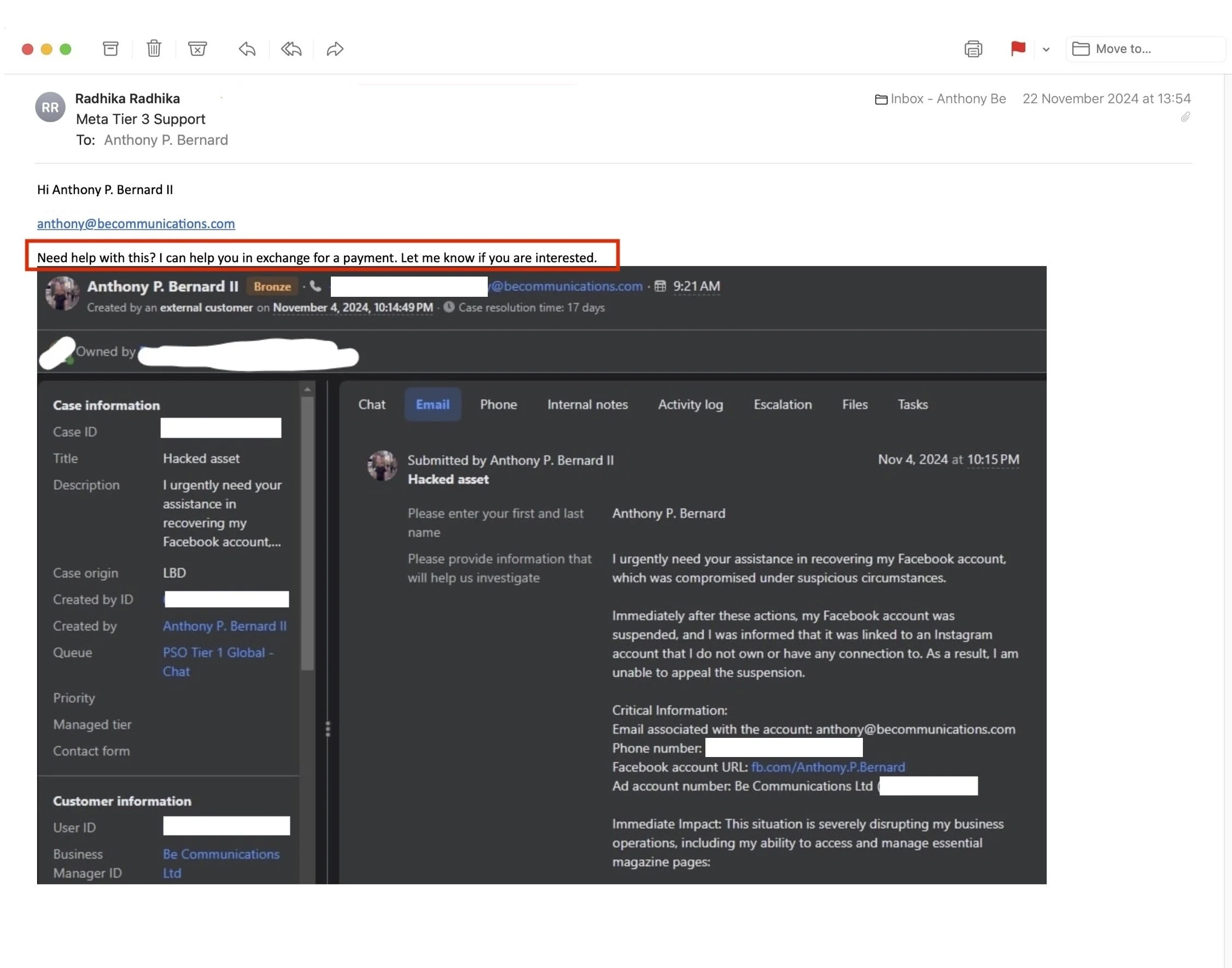
And then came the email that completely changed the tone. On 22 November, I received a message from a Gmail address using the name of a Meta Tier-3 support agent. The person quoted my correct phone number, referenced my existing case, and attached a screenshot from what was clearly Meta's internal support dashboard. The offer was blunt and straightforward: they could fix my problem, quickly, in exchange for a payment of '1-2k USD negotiable'.
Attempted bribe
Up to that point, I had assumed incompetence. That email introduced something darker: the idea that the chaos might be profitable for someone. I obviously refused and reported it through official channels. I never received a proper explanation. The case ticket moved on as if nothing unusual had happened.
Months passed. Then, finally, one of the support cases came back with a clear admission: Meta confirmed that my account and the connected pages had indeed been compromised. It was almost a relief to see it in writing. The problem is that confirmation did not lead to action. Nothing was restored. Access was not returned. The pages remained unreachable.
Later, another case concluded with the exact opposite statement: that there was "no evidence of compromise". Same account, same history, same screenshots, same everything – two incompatible decisions from the same company. It felt like dealing with a bank that both confirms and denies your card has been stolen in the same letter.
When Meta's internal mechanisms clearly weren't working, I escalated it to the outside. The Malta Communications Authority reviewed the situation and forwarded it to Ireland, where Meta is based. There, Coimisiún na Meán – Ireland's Digital Services Coordinator – passed it to ADROIT, an EU-certified dispute body under the Digital Services Act. ADROIT declared the complaint admissible and, in a very frank email, admitted they were facing "significant challenges" getting cooperation from some platforms. Meta was one of them.
By this point, almost a year had passed since the original hack. I had already decided to seek full legal representation. But there was one last twist before we crossed that line.
Meta escalated my case to a WhatsApp-based verification process – a kind of last-chance saloon in their recovery system. Through WhatsApp, they asked me to submit my ID again. They repeatedly confirmed that it matched their records. They sent me unlock links with expiry timestamps. I clicked one, and for the first time in nearly a year, I was able to log back into my old profile.
For about one minute.
Then the suspension notice returned, identical to the first one: my account was once again being penalised because of the same fictitious Instagram handle, the same machine-generated nonsense name that had never belonged to me. The system had accepted that I was me, then immediately punished me for being someone else.
That was the moment the frustration turned into something colder: resolve. Because by then I had spoken to enough people to know that others in my position had eventually succeeded. Some Maltese businesses that went the legal route did get their pages and ad accounts back, even after months of being told nothing could be done. It doesn't erase the disruption; it does prove that persistence and pressure work.
So I haven't stopped. The legal letter is drafted. Regulators are informed. ADROIT has my file. I'm still publishing, still running my magazines through new pages and fresh structures, but I've also accepted a hard lesson that every business owner should hear. If your company lives entirely on someone else's platform, then you are a tenant, not an owner.
This isn't just a story about a hack. It's about a system that can misidentify you, lock you out, contradict itself, ignore you, offer you a bribe through the back door, and then tell you there is "no evidence" of anything wrong. It's about a loophole that has existed for years, documented in public forums, affecting real livelihoods, and still somehow not treated as urgent.
And it's about refusing to accept that this is just how things are.
My access may be gone, for now. My patience may be thinner than it used to be. But my fight with Meta isn't over. If anything, it's only now getting to the interesting part – the part where they finally have to answer, on the record, how a fictitious Instagram handle and a broken appeal system were allowed to override a real person, an honest company and a very real business for this long.
If anything, this ordeal clarified one thing: owning your platforms — your website, your mailing list, your subscriber base — is no longer optional. Until Meta fixes the cracks in its system, small businesses in Malta need backup plans, shared-access structures, and a healthier relationship with where they build their digital homes.
Because once that front door slams shut, getting back inside is nothing short of a saga.
How to protect your business pages before a hack happens
1. Add multiple trusted admins
Never rely on a single personal profile. One lockout = entire business gone.
2. Separate personal and business identities
Use a Business Manager with role-based access, not your primary account login.
3. Backup 2FA codes physically
The most common failure point in account recovery is two-factor lockout.
4. Keep domain and email ownership updated
Meta uses DNS and email verification to confirm ownership during disputes.
5. Maintain your own platforms
Website, newsletter, database — your real assets. Social media is a rented space.
6. Monitor for suspicious login alerts
Many hacks show "Chrome on Windows" or unfamiliar regions — investigate immediately.
7. Document everything
Screenshots, timestamps, case numbers — this evidence becomes vital if recovery collapses into legal escalation.




















It's only been months since Alex Borg took the helm of the Nationalist Party, but the countdown to an election year has already started. In this wide-ranging interview with Vanessa Macdonald, he lays out his pitch to Malta's 100,000 non-voters, his plan to rebuild trust through structure and transparency, and why the PN must act like a "government in waiting" — not an Opposition on pause.